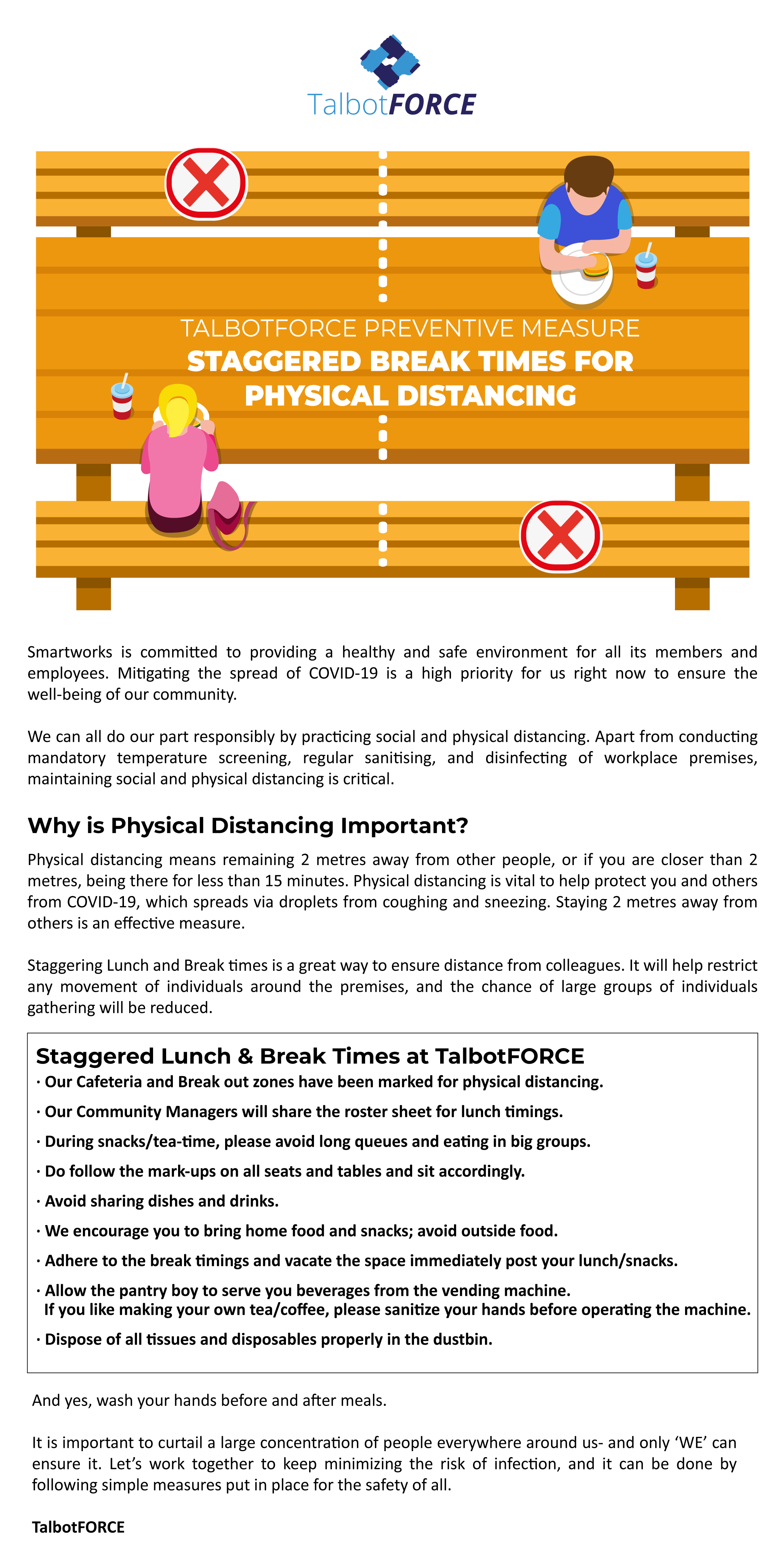
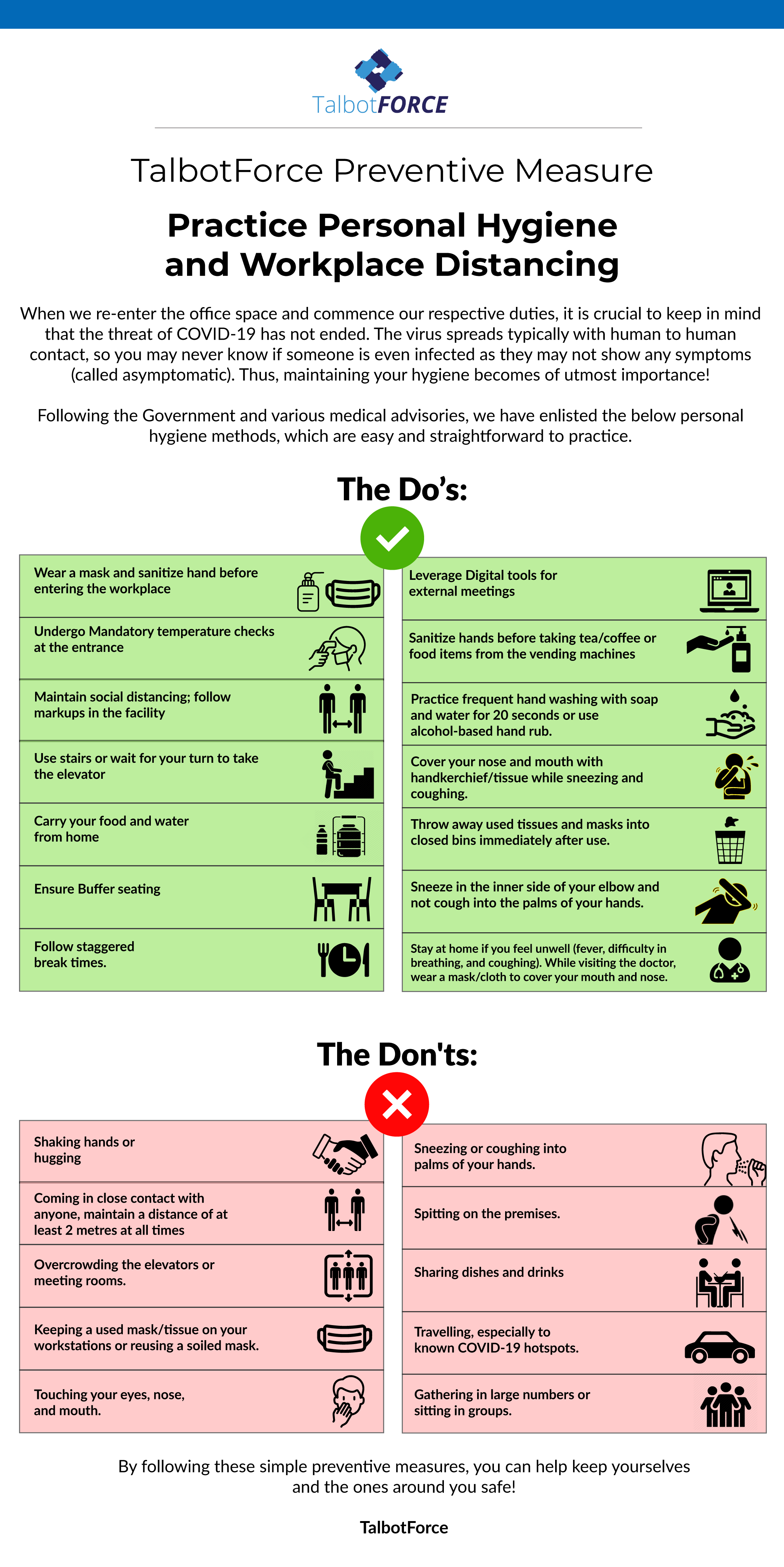
A security risk assessment is a regular intervention process that allows organizations to continuously detect, assess, and implement key security concerns in business applications. It prevents the data infrastructure and applications from security defects and vulnerabilities.
Timely and regular security risk evaluation is necessary for any organization to review its application portfolio holistically and prevent attackers.
The Key Procedure for an Effective Risk Assessment Framework Includes
Outline the requirements first step is to outline any business’s business, regulatory and contractual requirements to establish a transparent and measurable risk assessment framework. The second step is setting the risk gauge meter, a combination of the probability and effect of security occurrences. Basis the risk evaluation, develop the critical requirement and necessity for risk assessment to understand the risk and implement effective steps.
1. Identify Risks
An organization needs to have an upended understanding of its IT infrastructure and applications in identifying threats and exposure to risk. This helps in mapping threats to assets and vulnerabilities. The individual risk profile for each threat helps in gauging the risk parameters and helps in creating an effective counter-deterrence.
2. Prioritize the Risk
The individual risk profile helps map each threat’s intensity and assists in the prioritization of the threat. Rank each threat basis its intensity barometer in both its likelihood and its effect on the entire ecosystem. This gives a bird’s view of holistically analyzing each risk and finding an effective solution to every single risk, thereby maintaining a robust infrastructure.
You Read also: Things To Consider Before Hiring A Security Guard Agency
3. Taking Effective Measure
Once the risk and its intensity are identified, the next step is to take corrective measures to treat the threat. Effective treatment and alleviating the risk implements efficient use of team resources and avoids any disruption in the project. Hence the continuity of the projects is not disturbed, and the risk is mitigated efficiently. With time the businesses build an extensive database of past projects and risk logs that helps in anticipating possible risks and allow them to take more proactive steps rather than the reactive approach.
4. Screen the Risk
Only some risks need to mitigate or diminish from the system entirely, and certain risks stay in the system. Disciplined tracking and mapping of the risks are essential to screen the probability, and if any risk might appear, proactive steps could be taken.
Assessing security risks and threats is integral to any business security structure. This help in keeping the decision makers aware of the vulnerabilities in the system and possible effective steps implementation can secure the business infrastructure.